Full-disk encryption (FDE) is a low-effort way to ensure that if someone were to get ahold of one of your drives while unmounted or a Mac while powered down, the contents on the drive would be unusable to them without knowing a password or other encryption information. Apple offers two distinct ways of encrypting volumes on a drive, and it’s important to know the difference between them and the current limitation on drives connected to M1-based Apple Silicon Macs.
- FileVault: FileVault lets you control access to your startup volume, whether on an internal or external drive, including encrypting a drive where necessary. This can’t be used with an external startup drive with an M1-based Mac.
- Drive encryption: Finder-mountable non-system volumes can be encrypted via the Finder, as well as advanced ways via the command line and Disk Utility. You can encrypt a non-startup external drive’s volume on any Mac.
FileVault encryption
You can read the full details elsewhere on Macworld about the ins and outs of FileVault, but it’s a way to combine the security of account-based access with the assurance of fully encrypted data. FileVault is managed via the Security & Privacy preference pane’s FileVault pane.
How FileVault works varies based on your model of Mac:
- Intel Macs without a T2 security chip: These older Macs, largely models introduced before 2018, use FileVault both for startup security and to handle disk encryption. You can also use FileVault to encrypt and protect an external startup or bootable drive while it’s booted into macOS.
- Intel Macs with a T2 security chip: Most Intel Mac models released starting in 2018 have a T2 security chip, which is set to always encrypt the drive, even if FileVault is disabled. (There’s a way to disable this, but there’s no reason to.) The Secure Enclave handles all the necessary pieces. FileVault on a T2-equipped Mac protects a Mac’s data at a cold startup. With such models, you can also use FileVault on external bootable volumes, but FileVault handles the encryption in those cases.
- Apple silicon M1 Macs: The new M1-based Macs Apple introduced in late 2020 have a Secure Enclave module, and also always encrypt the startup drive. However, these Macs so far cannot correctly use FileVault on an external bootable volume. Unfortunately, you can turn on FileVault on an external drive, but on restarting, it’s no longer recognized. This likely has to do with the way in which M1 Macs boot from the system volume in Big Sur. Apple should either disable the capability or fix the problem.
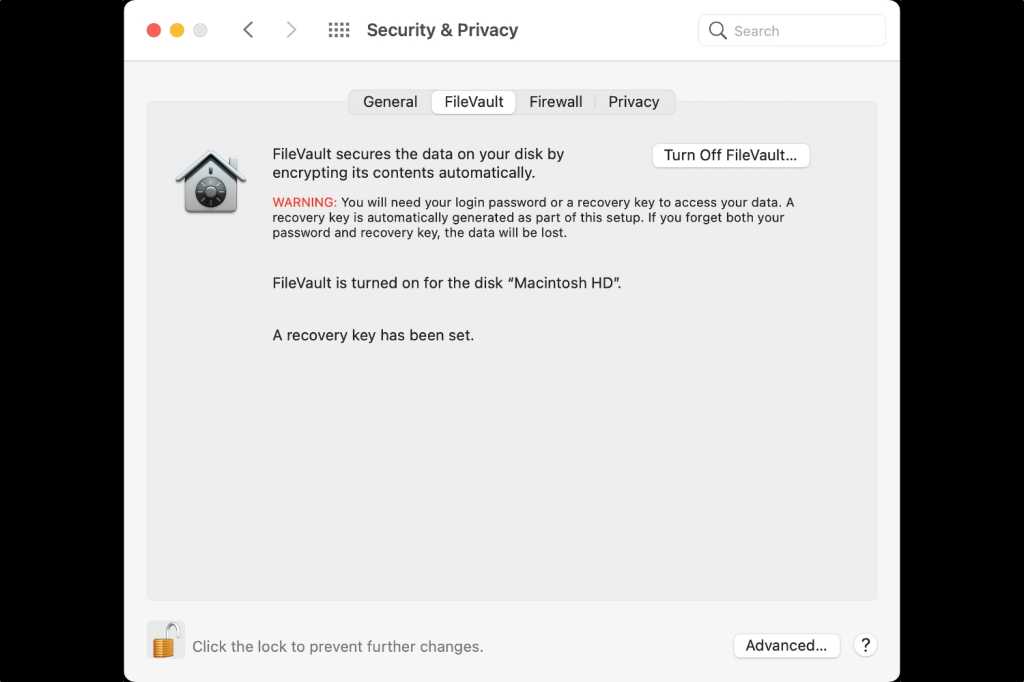
To turn on FileVault in macOS Big Sur, you activate it in System Preferences, under Security & Privacy.
Apple
When you enable or disable FileVault protection on a T2/M1 Mac’s internal drive, because encryption is always on, FileVault turns on or off immediately. With an external drive used with an Intel Mac, you can monitor the progress roughly from the FileVault pane of the Security & Privacy preference pane—or see below.
FileVault enables security when powered down for both pre-T2 Macs and T2/M1 Macs: it prevents access at startup without a password for a valid account on the Mac, or for any decrypted data on the drive if accessed in any fashion by another Mac or forensic-examination equipment.
Drive encryption
Entire volumes can be encrypted directly, but then they cannot be used to start up a Mac, because of how FileVault and the startup elements on Macs interact. Encrypting such drives is useful when you’re using them for storage and backups.
A drive with volumes encrypted in this fashion is fully available when mounted and the password entered. If you choose to store the password in the Keychain, then anyone who gains access to your unlocked Mac and can mount one or more volumes from the drive gains access as if the contents weren’t encrypted.
However, in these cases the encrypted contents are unavailable if no party but you has the password to your Mac or the volumes:
- You didn’t store the password for the volume or volumes and the drive is unmounted.
- You stored the password, but your Mac is powered down.
- You stored the password or the drives are mounted, but your Mac is locked. At that point, someone would need to overcome the hurdle of breaking into your running Mac.
You enable encryption on a drive very simply from the Finder:
- Control-click the drive on the Desktop or in a Finder window.
- Select Encrypt.
- In the dialog that appears, enter a password generated from your password manager or use the key icon to generate one within macOS. (Warning! Make sure you have a copy of the password stored securely for yourself, or the drive’s contents will be permanently inaccesible.)
- Enter the password in the Verify Password field, and then enter a password hint. I prefer to store my password securely and my hint tells me in which manager I stored it, like 1Password.
- Click Encrypt Disk.
- The disk typically needs to unmount and re-mount, and a background encryption process starts that can take hours or even days, depending on the amount of stored data and the encryption power of your machine.
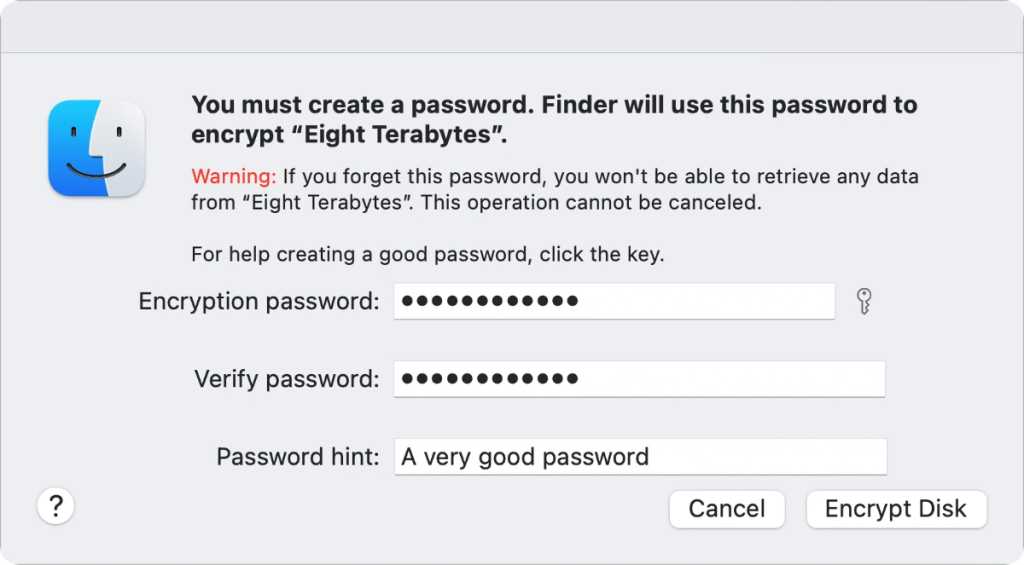
Enter and record the password for your external drive.
IDG
In Disk Utility, if you examine any volume that you’ve encrypted with macOS 10.14 Mojave or later, it shows up with “Encrypted” in the parenthesis for the volume type as “APFS (Encrypted)”. Disk Utility converts a volume that is formatted as Mac OS Extended (Journaled), otherwise known as HFS+, to APFS in the process, and uses the APFS (Encrypted) subtype.
An important side note: If you’re using any volumes on the drive as backup destinations for Time Machine in Mojave or later, directly from your Mac or over your local network, you don’t want to encrypt the drive. Only Macs with Big Sur can backup via Time Machine to an APFS-formatted volume. And, in testing, only HFS+ can be used as the formatting for a destination volume for networked Time Machine backups, whether the Mac being backed up is running Big Sur or an earlier version of macOS.
You can reverse the operation by selecting the drive, choosing Decrypt, entering the password, and then a similarly lengthy operation occurs to decrypt the drive. If it’s been converted from HFS+, it rem
For more advanced users, you can create encrypted volumes directly via Disk Utility or the command line, though this involves destructive erasure of volumes, containers, or partitions, depending on what you’re trying to secure.
Checking drive encryption status
With an Intel Mac without a T2 chip, with FileVault encrypting an external drive on any Intel Mac, or with any model of Mac encrypting an external non-startup volume, you can monitor progress by using a command-line tool. (FileVault’s progress bar isn’t that accurate.)
From Applications > Utilities > Terminal, type the following and press Return:
diskutil apfs list
This shows all the APFS containers and volumes, and the status of encryption in progress. You have to scroll through a lot with many disks and volumes to find that information, so you can instead type the following command to extract just the progress line:
diskutil apfs list | grep Encryption
That will match against lines like:
Encryption Progress: 69.0% (Unlocked)
Confusingly, when encryption is completed, whether it’s a startup volume secured by FileVault or an external volume encrypted via the Finder or other means, the diskutil app shows that encryption is enabled always as:
FileVault: Yes (Unlocked)
Ask Mac 911
We’ve compiled a list of the questions we get asked most frequently along with answers and links to columns: read our super FAQ to see if your question is covered. If not, we’re always looking for new problems to solve! Email yours to mac911@macworld.com including screen captures as appropriate, and whether you want your full name used. Not every question will be answered, we don’t reply to email, and we cannot provide direct troubleshooting advice.
Note: When you purchase something after clicking links in our articles, we may earn a small commission. Read our affiliate link policy for more details.
"device" - Google News
April 29, 2021 at 05:00PM
https://ift.tt/3t0spr5
How to encrypt a Mac storage device - Macworld
"device" - Google News
https://ift.tt/2KSbrrl
https://ift.tt/2YsSbsy
Bagikan Berita Ini














0 Response to "How to encrypt a Mac storage device - Macworld"
Post a Comment